Ehtereum Network Analysis — Part 05: Whale & MEV Methodology
Whale & MEV Methodology
Finally, the fun part.
This chapter covers how I detect whales and potential MEV‑style behavior in the network. Again, this is based on one day of data, so the goal is to demonstrate methods, not claim market‑level insights.
1. Whale Detection
A whale is defined here as:
- ETH transfer > $10k
- Token transfer > $10k USD equivalent
After filtering, I identify about 11 unique whale addresses in the dataset. Not a lot, but enough for research purposes.
1.1 Whale Ranking
Top value whale: 0x28c6c06298d514db089934071355e5743bf21d60 Top PageRank whale: 0xc02aaa39b223fe8d0a0e5c4f27ead9083c756cc2 Top degree whale: 0xc02aaa39b223fe8d0a0e5c4f27ead9083c756cc2 Top overlap whale: 0x28c6c06298d514db089934071355e5743bf21d60
1.2 Centrality-Based Whale Detection
deg = nx.degree_centrality(G_hetero)
pagerank = nx.pagerank(G_hetero)
High PageRank addresses are often:
- exchanges
- routers
- settlement contracts
2. Whale Ego Graphs
ego = nx.ego_graph(G_eth, whale_addr, radius=1)
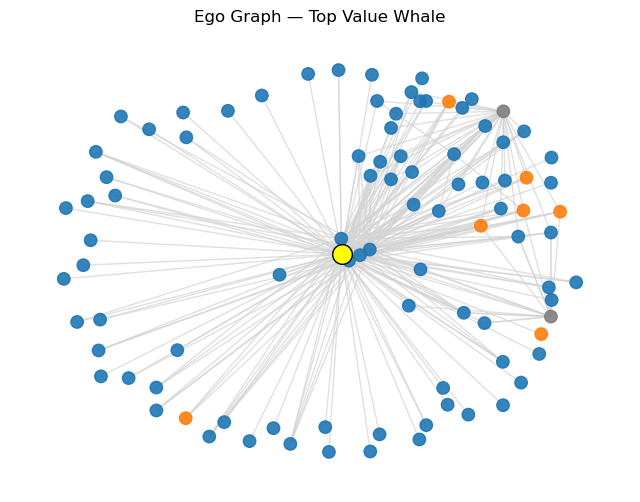
You can clearly see multiple inbound and outbound flows.
Net Flow: Value vs Centrality Whales
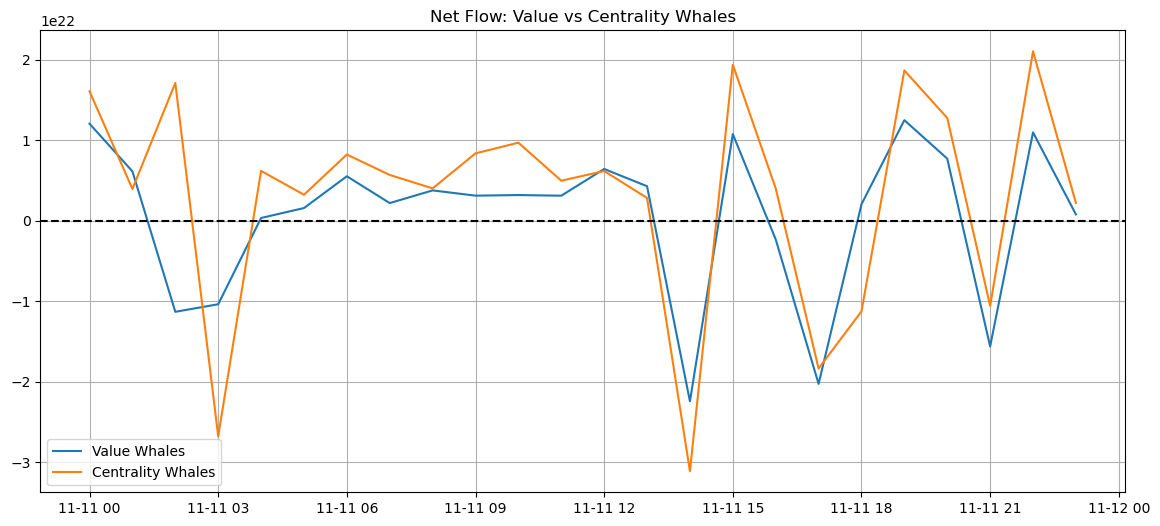
TODO
MEV Detection 3.1 Router Frequency 3.2 Time Interval Patterns
- Mini Case Study
